
Theoretically, blockchain’s use of cryptographic hashing renders it to be mathematically impossible to be hacked but there is a caveat here. Although blockchain is for all practical purposes indeed hackproof but as always there are exceptions to the rule. Case in point is the significant increase in the value of losses due to crypto hacks from 2020 to 2021 with this trend being set to continue in 2022. It should be noted however, that 2021 was a particularly bad year for the crypto market in terms of hacks statistics. There were 250 hacks in 2021, which was almost 5 times more than the year before. The largest of these hacks was the USD611 million exploit of the PolyNetwork.
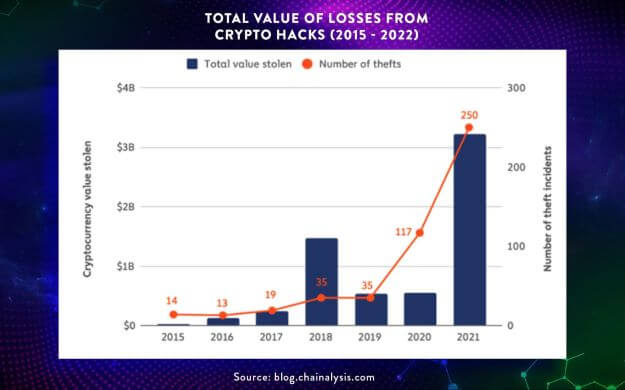 Total Value of Losses from Crypto Hacks (2015 - 2022) (Source:blog.chainalysis.com)
Total Value of Losses from Crypto Hacks (2015 - 2022) (Source:blog.chainalysis.com)
Statistically, the number of crypto hacks have been on the rise over the past few years. Case in point is the fact that the total number of crypto hacks recorded a Year-on-Year (YoY) increase of more than 100% from 2020 (117 hacks) to 2021 (251 hacks). In terms of cryptocurrency value stolen as a result of these hacks, DeFi platforms bore the brunt, accounting for more than USD2 billion of the USD3.1 billion of cryptocurrencies lost. This figure is much higher than the USD1.7 billion in financial losses suffered in 2021 by seniors in the U.S who are particularly vulnerable to frauds and scams.
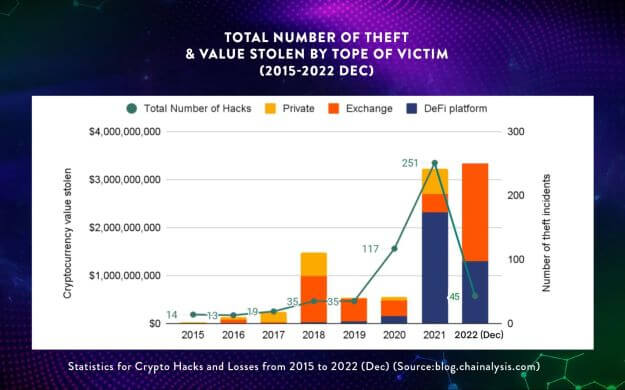 Statistics for Crypto Hacks and Losses from 2015 to 2022 (Dec) (Source:blog.chainalysis.com)
Statistics for Crypto Hacks and Losses from 2015 to 2022 (Dec) (Source:blog.chainalysis.com)
In case you are wondering why DeFi platforms are so much more prone to hackings than CEXs, it's because DeFi platforms stay true to the decentralization and transparency ideals of blockchain by operating using open-source protocols. The open-book nature of the program codes of DeFi platforms is akin to Christmas coming early for cyber criminals who can have a field day looking for security vulnerabilities in these codes. Once cyber criminals manage to find any security vulnerability, they would exploit these vulnerabilities to breach the security framework of DeFi platforms. This results in security breaches and code exploits which together constituted almost 100% of the crypto losses in Q1 2022.
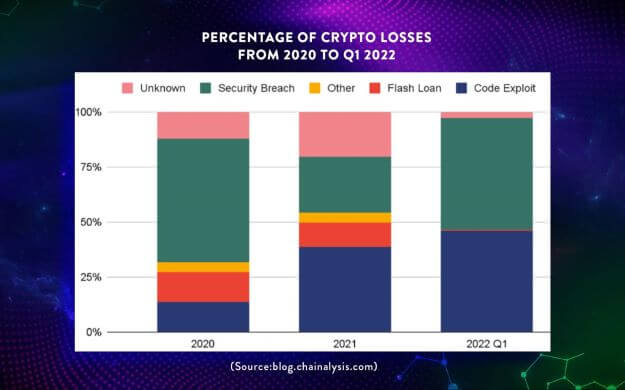 Percentage of Crypto Losses from 2020 to Q1 2022 (Source:blog.chainalysis.com)
Percentage of Crypto Losses from 2020 to Q1 2022 (Source:blog.chainalysis.com)
At this juncture, some may think that only DeFi platforms are at risk of being hacked but centralized exchanges (CEXs) too are vulnerable to such risks with top CEX Binance being the latest and arguably the most prominent victim in October 2022. A security vulnerability in the smart contracts of Binance’s cross-chain bridge was exploited by hackers who managed to make off with 2 million Binance Chain (BNB) tokens which were worth about USD570 million at the time of the theft. Besides Binance which had previously suffered a USD40 million hack in 2019, other top CEXs including Crypto.com, Coinbase and KuCoin were also not spared by hackers.
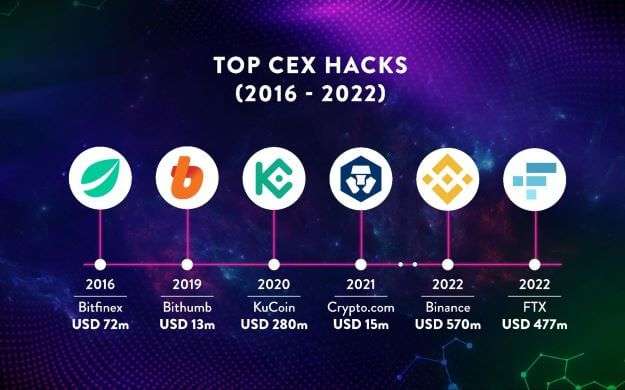 Top CEX Hacks (2016 -2022) (Source: AvocadoDAO)
Top CEX Hacks (2016 -2022) (Source: AvocadoDAO)
The list of hackings of custodial wallets including those involving Liquid (USD97 million), AscendEX (USD80 million), and BitMart (USD150 million), all 3 of which occurred in 2021 highlights the dangers of such wallets. In terms of the alternatives, there are 2 types of non-custodial wallets i.e. hot and cold wallets. In contrast with cold wallets where private keys and crypto assets are stored offline, the private keys and crypto assets of hot wallets are stored online. The three top brands of cold wallets in the market are Ledger, Trezor and Ellipal whose top of the line models are Ledger Nano X, Trezor Model T and Ellipal Titan Bundle respectively.
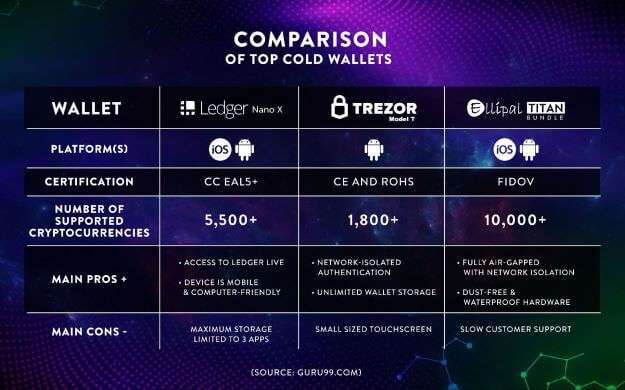 Comparison of Top Cold Wallets (Source: guru99.com)
Comparison of Top Cold Wallets (Source: guru99.com)
Custodial wallets on the other hand are generally exchange wallets which require trust to be reposed on a third party.
 Common Cryptocurrency Wallets (Source: dbs.com.sg)
Common Cryptocurrency Wallets (Source: dbs.com.sg)
In terms of their pros, both hot wallets and custodial wallets are convenient and easy to use with the latter having the upper hand in this regard. Nonetheless, cold wallets offer the highest level of security thanks to their offline storage functionality. As for their cons, both hot wallets and custodial wallets are more susceptible to hacks than cold wallets. However, the better security of cold wallets comes at the price of their relatively higher costs and greater usage inconvenience.
Regardless of their choice of wallet, crypto users would do well to protect their digital assets from the ever-present risks of hackings by following these best practices for the storage and handling of their cryptocurrencies:-
Best Practice #1: Do not connectIf you choose to store your cryptocurrencies in cold wallets which operate in an offline manner, this disconnection from the Internet significantly reduces the risks of falling victim to hacks. When it comes to staking, opt for cold staking i.e. non-custodial staking whereby you can stake your crypto assets in an offline manner using your cold wallet.
Best Practice #2: Do it rightIf you choose to use a hot wallet, use strong passwords and activate multi-factor authentication such as two-factor authentication (2FA). As for your private keys, back them up together with your mnemonic phrase preferably in separate hardware locations. If and when you do connect your hot wallet to the Internet, make sure this is done via a private and secure network whereby public WiFi networks are definitely no-nos.
Best Practice #3: Do your researchIf you choose to go for usage convenience with custodial wallets, be sure to do your research into the security background and credentials of the service provider. A good source of reference would be blockchain security platform CertiK which has a designated trust score for most crypto service providers.
Other than the above mentioned dos and don’ts, some additional tips to protect yourself against crypto scams and hacks are:-
Tip #1: Verify the legitimacy of websitesMake sure that the websites you are browsing are legitimate by using the organic search function on similarweb.com to verify that the websites are the official sites of the merchants or service providers you are looking to patronize.
Tip #2: Verify the legitimacy of Telegram channelsGiven the plethora of scams making their rounds on Telegram particularly through fake channels, you may want to avoid sourcing for information or entering into any transaction through Telegram as the counterparty may turn out to be an impersonator. Always look for the blue tick beside the profile name as this indicates that it is the official account of the company as verified by Telegram. Additionally, a telltale indication of an impersonating Telegram account is a lack or absence of real life organic conversations between members of the group. You should refrain from clicking on any links or entering into any transactions with anyone from such Telegram accounts.
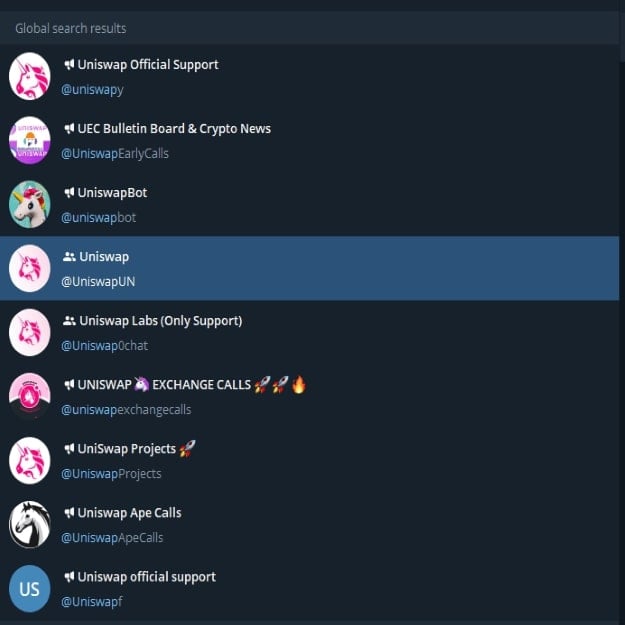 Impersonating Accounts of DeFi Platform Uniswap (Source: Telegram)
Impersonating Accounts of DeFi Platform Uniswap (Source: Telegram)
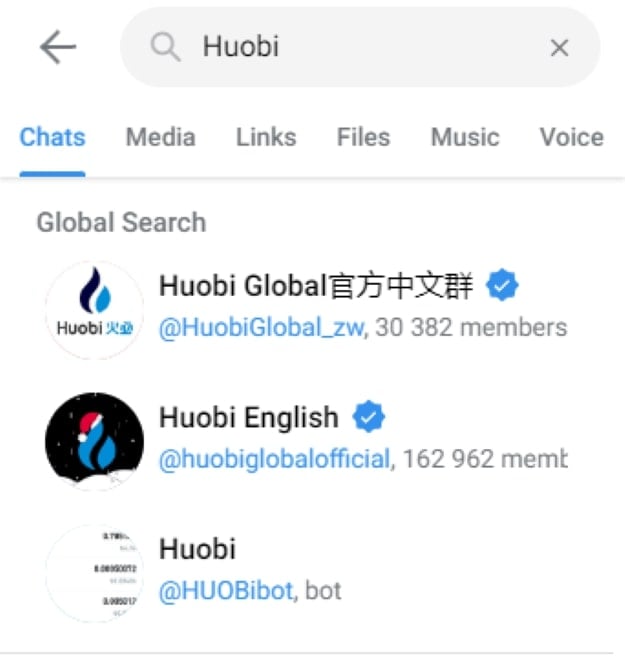 Verified Official Accounts of CEX Huobi (Source: Telegram)
Verified Official Accounts of CEX Huobi (Source: Telegram)
When undertaking Google searches, refrain from clicking on advertisements but instead go straight to the search results. You can tell which items are the advertisements and which items are the search results by looking out for the word “Ad” that would appear on the right side of the advertisement items. In terms of their placement, advertisements would appear at the top of the page followed by search results.
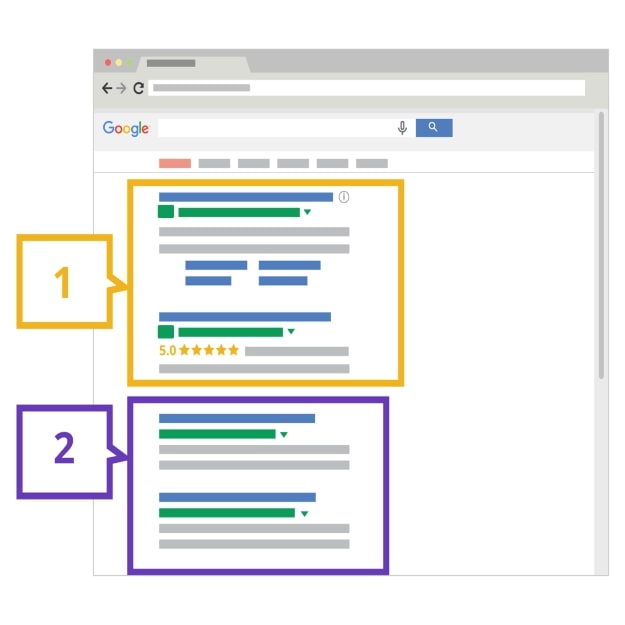 *1 = Ads , 2 = Search results (Source: support.google.com)
*1 = Ads , 2 = Search results (Source: support.google.com)
Abstain from clicking on links or opening attachments in emails from non-trusted sources as a common phishing method is to trick victims into clicking on malware infected links or opening fraudulent attachments.
(4) ConclusionIn many ways, the prevalence of crypto hacks is one of the many growing pains of the industry as it charts its way towards becoming a mature financial market. As we await the dawn of the crypto era of stability and security, crypto users can hackproof their digital assets by duly adhering to the best practices for the storage and handling of these assets.
The information in this article is neither intended as nor amounts to financial, tax, legal, investment, trading, or any other form of professional advice. Avocado DAO makes no representation whatsoever that the information herein is accurate, up to date, or applicable to the circumstances of any particular reader or organization.
The use of the information herein is entirely at the reader's own risk, who shall assume full responsibility for the risk of any loss or damages arising from their reliance on such information. For the avoidance of doubt, under no circumstances is Avocado DAO to be deemed as having assumed responsibility or be held liable for any loss or damages, whether financial or otherwise, arising from the reader's use of or reliance on the information herein.